
How to choose best secure password
Cyber Security
With the latest thing of mechanical headways, we presently store essentially the entirety of our information on the web, making…
Current issues and insights on cyber security and IT security: risks, threats, internet security measures

How to choose best secure password
Cyber Security
With the latest thing of mechanical headways, we presently store essentially the entirety of our information on the web, making…

DuckDuckGo now stops Android Apps from snooping on your data
Cyber Security
Assuming you're worn out on the applications on your Android gadget stubbornly following each move you make even in the…

“Security software company McAfee acquired for $14 billion “
Cyber Security
Security programming association McAfee is going private through a buyout from a monetary patron gathering in a plan regarded at…

Apple ID: A Few Tips to Increase your Account Security Level
Cyber Security
In this day and age, online security has become an extremely important part of our everyday life. The risks associated…

New Android spyware masquerades as verified apps
Cyber Security
Security scientists have uncovered another spyware crusade that is focusing on South Korean occupants with Android gadgets to take…

Why Google is forcing people to use 2FA?
Cyber Security
Google is starting to drive a part of its record-holders to turn on two-part approval (2FA), according to a couple…

Temporary Access Pass in Microsoft Azure AD: A Guide to the Configuration
Cyber Security
Microsoft Azure Active Directory, or AD in short, allows you to sign in without the need of a password. This…

Google will enable two-step verification for over 150 million accounts by the end of the year
Cyber Security
We are presently in Cybersecurity Awareness Month as Google calls attention to in another blog entry, and as the hunt,…

Why am I not receiving my verification code from Google?
Cyber Security
Being a Google account holder, you can just appreciate a lot of administrations proffered by Google to clients that can…

Is there a way to find out who is behind a fake Facebook account?
Cyber Security
Assuming you need to distinguish a phoney Facebook account, then, at that point, you need to check out a couple…

Turn on Restricted Mode to Let Your Children Watch YouTube Videos Safely
Cyber Security
The Internet is a wonderful place for discovering new things, connecting with the people of your life and consuming content…
How to secure your Apple and iCloud accounts
Cyber Security
With high-profile information hacks consistently hitting the features, you may be considering how you can deal with protecting your own…
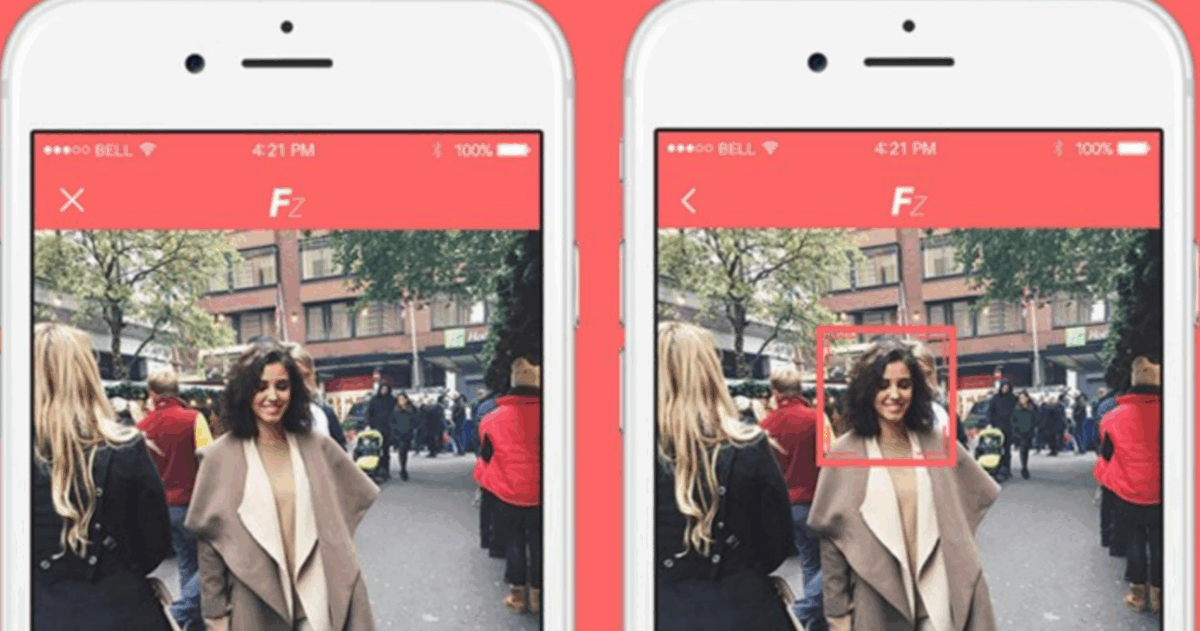
How can I prevent people from tagging me in their Facebook
Cyber Security
Labelling is a component given by Facebook to make a connection of the post on labelled individual profiles. It's an…
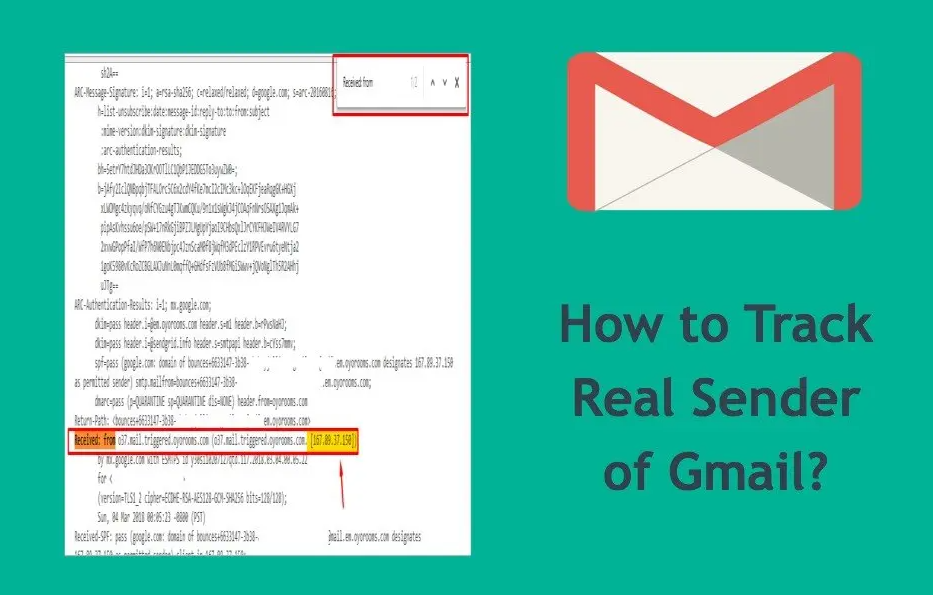
How to Track the IP Address of the Senders Email in Gmail
Cyber Security
Email is one of the most significant and utilized methods for correspondence to stay in contact today. These messages that…

How to find lost android phone from iPhone
Cyber Security
There are a modest bunch of telephone recuperation or hostile to burglary applications on the Google Play Store which can…

Find Out Who’s Calling you with Sync.Me
Cyber Security
Have you been receiving unwanted calls from unknown phone numbers throughout the day lately? Wouldn't it be nice to finally…

Hide your Google Account Info from Other Users in a Few Easy Steps
Cyber Security
If you own a Google Account, you'll certainly be content to learn about ways in which you can enjoy some…