
How to Set Parental Control in Google Search
Cyber Security
Accessing the Internet is very simple and with the multiple tools provided by the different platforms, its use has become…
Current issues and insights on cyber security and IT security: risks, threats, internet security measures

How to Set Parental Control in Google Search
Cyber Security
Accessing the Internet is very simple and with the multiple tools provided by the different platforms, its use has become…

Find your Lost Android Device with Google Find My Device
Cyber Security
Losing the phone sounds like a nightmare to most people in this day and age. Our mobile devices have become…

Forgot your TikTok Password? Follow these Steps to Reset it!
Cyber Security
When you create an online account, two things are universally regarded as the necessary credentials for logging in: a username,…

Top 2021 Tech Trends to Shape Future Investments
Artificial Intelligence
Cyber Security
One of the most extensive technological booms is happening around us right now. Every few months, we see a new…

My Instagram Account got Hacked: What Now?
Cyber Security
A social media account is something that billions of people around the globe have in common in this day and…

Can You Report a Bad Website to Google?
Cyber Security
The World Wide Web is a place full of options you can choose from, and by options we mean websites.…

How to delete your Gmail account permanently
Cyber Security
Are you trying to clean up your online footprint? Do you have a few extra email accounts that you could…

Is There a Safe Distance from your Wi-Fi Router?
Cyber Security
Have you ever wondered how Wi-Fi works? Of course, you know that connecting your computer or mobile device to a…

What to do When Firefox is Already Running but Doesn’t Respond
Cyber Security
One day, you turn on your computer and click on the Firefox icon to go on the Internet, as per…

How to Spot a Tinder Scammer
Cyber Security
Tinder is an online dating platform that can be used to find your so-called-soul mate. It is a very successful…

How to Reset Facebook Settings
Cyber Security
Changing your Facebook settings empowers you to accomplish an altered Facebook client experience that works for you and your business.…

The 5 most popular online scams to be aware of in 2021
Cyber Security
Online scams are a problem that has been occurring for a long time, where vulnerable people or people with certain…

Best TOR Alternatives for Anonymous Browsing
Cyber Security
The onion router, better known as TOR, is the search engine on the dark internet network. Dark networks are primarily…

How to protect your Google account with 2-step verification
Cyber Security
Two-factor validation (2FA) alludes to two stages you should take to get into an online record after you enter your…

How to password protect an Access Database
Cyber Security
Microsoft Access is one of the most in-demand products within your application suite. It is software that manages database. This…
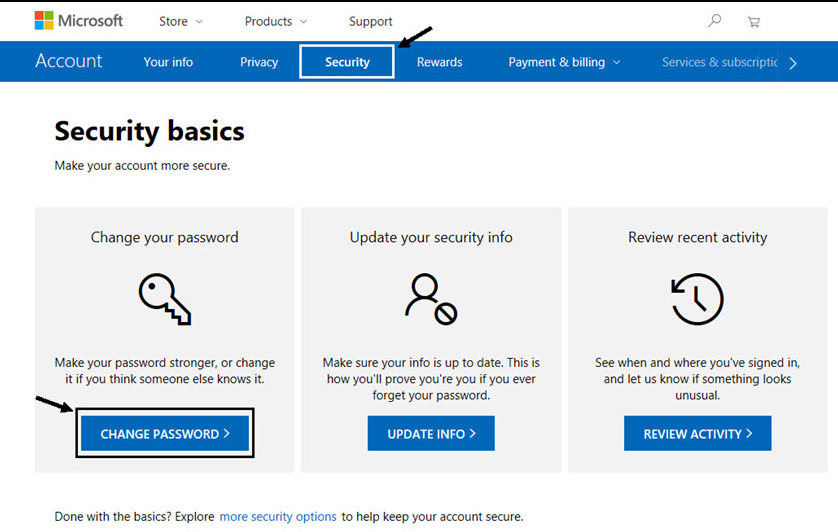
How to verify and make Microsoft account secure
Cyber Security
There is an assortment of reasons why you may utilize a Microsoft Record. You may utilize a Microsoft Record to sign…